
1. Overview: Job Responsibilities, Salary, and Common Requirements
2. A Comprehensive Guide to Becoming an Information Security Analyst
3. What Does an Information Security Analyst Do?
4. Signs You Should Consider Becoming an Information Security Analyst
5. How Do You Become an Information Security Analyst?
6. What are the Knowledge and Skills Needed to be an Information Security Analyst?
7. Popular Schools and Colleges in the U.S. for Aspiring Information Security Analysts
8. How to Get a Job as an Information Security Analyst
9. Learn About Geographic and Location Pay Differentials
10. Make Your Resume Stand Out
11. Ace Your Information Security Analyst Interview
12. Top Online Courses for Aspiring Information Security Analyst
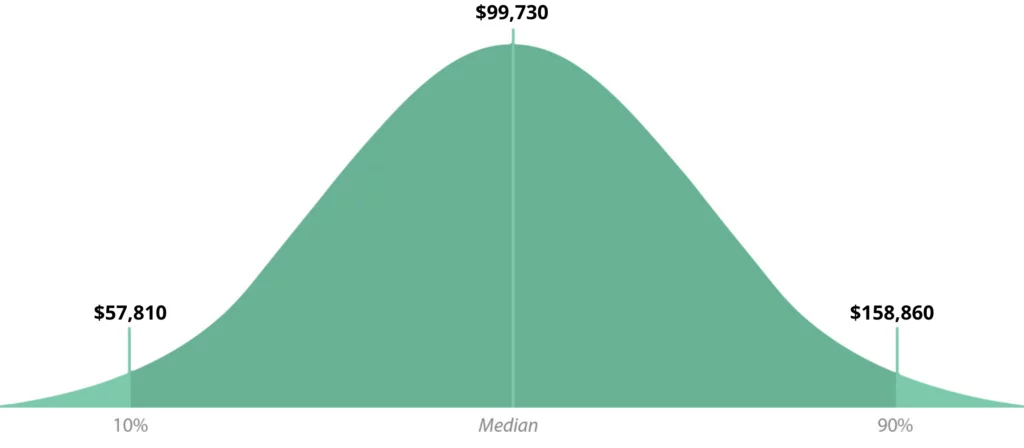
Information security analysts made a median salary of $99,730 in 2019. The best-paid 10 percent made $158,860 that year, while the lowest-paid 10 percent made $57,810.

Computer Information Research Scientists
Computer and Information Systems Managers
Computer Programmers
Computer Support Specialists
Network and Computer Systems Administrators
Programming languages
Operating systems
Network Security
Information Assurance (IA)
Systems and network configuration
Cryptography
Ethical hacking
Problem-solving skills
Communication skills
Detail-oriented
A company’s information systems are one of the greatest treasures any company protects. With this digital era, anyone can infiltrate such sensitive data through their mere fingers. That’s why companies tend to the help of IT experts called information security analysts who will serve as the gatekeepers of their information systems.
Cyberattacks are pretty common these days–in fact, it happens every 39 seconds according to a study at the University of Maryland. That number is alarming, making any company, big or small, vulnerable to threats such as breaches, infiltrations, hacks, and other cyberattacks.
The role of an information security analyst is to make sure these circumstances never happen. In some cases, it is not preventable, and cyberattacks have grown in number over the years. However, it is their responsibility to outsmart these hackers and maintain the security of the information systems of an organization.
The job demand for information security analysts is increasing more than the average for any other occupations. Having a 31% job outlook for the year 2019-2029 as per the U.S. Bureau of Labor Statistics (BLS), it is a career worth pursuing as IT jobs continue to be on-demand. So if you have always been so keen on pursuing this career, you should read on to find out everything you need to do to get there.
Information security analysts are the gatekeepers of the computer networks and information systems of a certain organization. They create preventive measures to avoid any harmful infiltrations that can leak any confidential data of a company. They carry the sole responsibility of making sure all networks’ security are intact and cannot be penetrated by any unauthorized access.
Information security analysts have a wide range of tasks that include the following:
So you’ve been wanting to be an information security analyst, but have you figured out yet the innate qualities that can make your career fare well in this industry? Here are some of the signs that can prove that this career is worth exploring for you:
First off, as someone who will be spearheading the cybersecurity of a company’s data, you are expected to be the expert of the technological aspects of securing them. If you are one who cannot wait to get his hands on the latest innovations to try them out, then you will surely do well in being an information security analyst as you are tech-savvy.
Do you have the appetite for learning what’s beyond the surface? A drive to gain new knowledge is a powerful aspect that will make you successful in pursuing an IT career like this.
In this kind of career, you should not be someone who slacks off and settles for what he already knows. Instead, you should be the one who dives first into learning what’s new.
With the fast-evolving advancements, someone who can keep up with this is the perfect person to handle the role. If you enjoy the dynamics of technology, you will do well in an environment that breathes in the constant change of modernization.
Having a keen eye to even the smallest detail is a highly valuable trait in being an information security analyst. This role requires the eye for spotless preparation and execution as cybersecurity is a very critical responsibility.
Are you a person who always takes into consideration all the possibilities that can ruin your plans? If so, you are built for a role like this. As an information security analyst, you will be needing the mind of someone who foresees everything and makes sure that there are contingency plans for any unexpected circumstances.
Working in an environment that deals with sensitive data of an organization carries the heavy load of making sure these aren’t hacked in some way. You will take the blame if any strategic scheme gets penetrated by unforeseen perpetrators. A strong stomach for a pressured environment is needed to survive in a career like this.
Having developed a strong barrier against hurtful words will play to your advantage in this career. Bosses tend to spit out upsetting words when unfortunate circumstances like system breach happened. They will blame you and you should have the emotional stability to deal with it.
All careers will require you to be able to speak up and interact with your colleagues. However, being an information security analyst demands you to break down the technical terms into simple statements that everyone on an organization will understand. Not only will you need to be articulate on the methodological processes of your role, but you also need to be good at your interpersonal skills.

So how does one become an information security analyst? Ranking 5th in US News & World Report’s best technology jobs in 2020, this career has a lot of opportunities in store for any aspirants out there.
Here is the series of requirements you will need to meet in order to be a successful information security analyst:
The first requirement to work your way up as an information security analyst is to hold a degree in an IT-related program. Programs like computer science, information technology, software engineering, cybersecurity, and other related fields provide the perfect ground for learning the fundamentals up to the advanced knowledge of information systems.
Though it is not required, holding an MBA in Information Systems sets you apart from those who don’t. It demonstrates your competency in your expertise as you have taken the time to pursue a higher level of education. Having an MBA gives you an edge over the others when looking for a job as employers prefer those who have it.
Your first experience will most likely be from your internships. Internships provide you a good training ground for the things that may not be learned inside the four corners of a classroom. You will be given the opportunity to tackle real-world examples of data security processes which will expand your knowledge and skillset.
In addition, you will need to earn an ample amount of working experience in the IT field as the role requires having familiarity in your work. You may start out as an IT professional, and work your way up as an information security analyst once you have specialized in it through years of experience or gaining certifications.
Certifications are highly preferred when looking for a job as an information security analyst. Although they are totally not a requirement to penetrate the job market, being specialized in one IT field adds to your credibility. These are some of the certifications you can get to boost your qualifications as an information security analyst:
In order to be successful in the field of IT, there are a lot of expectations an information security analyst should live up to. Both hard and soft skills go hand in hand to completely fulfill his duties. Here are the skills and knowledge an information security analyst should shave:
As a highly technical job, here are some of the hard skills that make an information security analyst adept to his job:
Also called “penetration hacking,” this aims to identify the network’s vulnerabilities through penetrating into the system itself. This way, any malicious threat that a hacker may take advantage of will be fixed immediately.
These are the systems designed to block any unauthorized access to a network.
This is the overall management of a network’s security to avoid any unauthorized access, modification, and misuse of resources. This includes various practices and adherence to security policies to protect the underlying network infrastructure.
The most used open-source operating system, Linux lies underneath the software of a computer and serves as the receiver of requests from its programs and relays them to the hardware.
The creation and generation of codes that will allow you to protect your data private. This converts data into an unreadable format so that any unauthorized eyes cannot pry on it.
Unix is an operating system (OS) that originated from 1969. It is the first operating system that was written in C language. It is a multi-user OS where the same resources can be shared by various users.
Cisco systems leads the network market through their number of products ranging from networking hardware, telecommunications equipment, to various IT products and services.
This is a general-purpose programming language used for designing both desktop and web applications.
The practice of providing protection and managing risks that relate to the use, process, storage, and transfer of data and information systems. Its process ensures the functions of availability, integrity, authentication, confidentiality, and non-repudiation.
Serving as the communication language of the internet, TCP/IP allows one computer to talk to another computer through the Internet by gathering network packets of data and sending them to the right location.
This refers to the process of setting up one’s operating system and networks’ control and flow to support the network communication of the owner.
On the other hand, here are the soft skills that make an information security analyst successful in his career:
One of the needed skills to fulfill the duties of an information security analyst is being an effective communicator. Knowing that you are working in the IT field and you are dealing with technical terms that most people in your work cannot understand, you have the responsibility of simplifying things for them.
Additionally, you are talking to colleagues that come from the different levels of the organization so strong communication skills is an essential part of performing your duties.
Having assigned to monitor the system and network of the organization, information security analysts have the keen eye for every detail imaginable. They are safeguarding a sensitive property of an organization which makes them responsible if any mishandling happens. Thus, an eye for detail is an essential trait to excel in this career.
As an IT career, it would not make sense to have somebody who does not keep tabs on the latest technology trends. What the industry needs is a person who has genuine interest for the IT field and doesn’t see this trait as a responsibility.
Being able to see the unexpected events that may come out is what makes an information security analyst thrive in his job. Remember, you are securing a series of networks–you have the responsibility of assessing everything that could go wrong and preparing contingency plans if they happen.
The thirst to learn more plays a vital part in this career, you will be needing continuous learning as the world of technology is fast-changing. Anyone in the IT field knows that you have to keep up and be able to adapt easily when there’s an innovation that could be of big help to you and your company.
Want to know the best schools that offer undergraduate programs or aspiring information security analysts? Check out Cyber Security Degrees’ list of the best schools specializing in cyber security and information assurance you can take into consideration upon pursuing this career:

In an era that relies on the latest technologies, jobs in the IT field are nowhere dropping in the near future. You are lucky to have a lot of career opportunities on your door–you just have to know where to knock. Here are some ways on how you can score your job as an information security analyst:
One of the most effective ways to source jobs is by asking your professional network if they happen to know any job opportunities for you. These people consist of friends, former professors, previous colleagues or mentors who can hook you up with a referral. Keep in touch with people in your field to add your chances of finding jobs easily. One of the most used platforms to get in touch with your network is through LinkedIn which you most probably have already.
All industries use computer systems and networks, so basically you have everywhere to look around. It’s just up to you where you would want to apply. You can list down first which companies you are eyeing and try to look them up online if they have openings. Then, you can add more options by scouring through the local job listings that may catch your eye.
The quickest and easiest way to find a job is through looking up online job portals. These online platforms have a wide range of opportunities you could look into. You may check out this list of popular online job search portals that can help you scout potential employers:
While you are at it, you should look up specialty websites that are specifically made for IT-related jobs which include:
Job fairs happen every once in a while at nearly every location in the country. This kind of event is pre-scheduled so it’s good practice to watch out for them in time of your job search. In order to know the schedule and location for this, you can look at their websites to be notified.
Here are some of the websites to check upon looking up for career fair updates:
Having an impressive pay of $99,730 annually, information security analysts’ annual pay still differs based on the location they are in. This is the list of how much they make annually on each state:
Report from the Bureau of Labor Statistics
How you construct your resume speaks a lot about you. Create a good first impression by crafting a resume that reflects your personality and expertise in the field. After all, your resume is the first thing that a potential employer sees, so you ought to make the most of it.
To help you strike a good impact on them, here are a few pointers on polishing your resume:
A career objective is an elemental part of the resume that aims to introduce you and give an overview of what you want to pursue in the future. A three-sentence paragraph can suffice to provide your interviewer with who you are, what you can do, and what you are aiming to do in the next couple of years. Every resume starts out with a career objective, so make sure you put in the effort to make it count.
Time to show them what you are capable of! Enumerate in a concise manner your skillset and knowledge. You can go first with the hard skills you have dexterity in, and then go on to the soft skills that meet with the role.
Ensure that the skills you are listing down match the job requirements of the role you are applying for. Also, add some valuable assets that you know will boost your credentials.
Whether it is your first job out of school or you’ve had a handful of experience, you will be needing to list down your past experiences in reverse-chronological order. This way, you are showing to your potential employer the overview of what experiences you had, how long you have worked, and how much time you spent at one company. Looking at this information will help them assess if you are one to stay at a company or not.
In addition, you should support those experiences by giving a brief summary of what duties you’ve handled. Interviewers will want to know how familiar you are with the tasks that make up the role of an information security analyst.
To be an information security analyst, attaining a bachelor’s degree in any IT-related program is required. List the details down on your resume and add any other additional educational training you have obtained. Impress your interviewer with these credentials. If you’ve got an MBA, that’s even better as most employers will prefer someone who has it.
Certifications are a big deal in cybersecurity careers. They do not only boost your qualifications, but they also display your adeptness at the specialization you are in.
Here are some of the most sought after certifications for information security analysts:
Being affiliated with professional organizations is one way to impress your potential employer. You can be an active member of a number of associations relevant to your expertise.
Here are some professional organizations that you can consider:
You are now on the last step to landing your role as an information security analyst, make sure you exert the utmost effort to nail that interview. Here are some of the technical questions that can be thrown your way:
The first question related to your responsibilities would most likely be this. So what are your duties? Any interviewer is interested in how familiar you are with the tasks and what your expectations are in fulfilling your job. Be able to provide an overview of your expected tasks that revolve around ensuring the security of computer systems and networks.
The duties you shall discuss include implementing security measures to protect the network, assessing any vulnerabilities that may pose threat, installing and updating various security software needed, running tests to discover any potential harms, preparing network disaster plans, promoting network security protocols to users, keeping up-to-date with the latest security trends, suggesting security enhancements and updates, and more.
This question demands to know how up-to-date you are with the latest trends in the industry. You are expected to incorporate modern technologies with the network security you are guarding so being in the loop matters. You will not have any problem sharing with the interviewer what you know if you are genuinely invested in your field. Just prepare yourself to identify the latest news and trends you highly think are valuable to network security.
This is a test of your knowledge on your roles as an information security analyst, so you should know by heart how to properly run network security. Having said that, you are aware of the risks that pose threats to any safeguarded information systems. You should enumerate them to your interviewer and briefly explain how they pose a threat to your data.
Some of the answers will include users who neglect security policies, personal devices that are connected to the network, users’ use of public cloud applications, employees working offsite and using insecure connections, and more.
To prove your experience, they will inquire about any previous encounter that you can elaborate to them. This question wants you to demonstrate your problem-solving skills. Display your skills by being articulate with the situation and ensure your methodological processes are logical.
Data leakage happens when data is separated from its intended storage. The reasons it happens may vary from a system breach, human error, corrupt hard drive, insecure backup storage, insufficient security control from shared drives, technological errors, to system misconfiguration. There are tons of reasons why this vulnerability can happen–enumerate as much as you know.
These are just some of the technical questions that may come up, and there are still lots of other aspects that an interview would like to look into. You just have to prepare yourself to properly answer these questions, and once you have properly delivered a good set of answers, you are just one call away to securing your coveted job.
Sharpen your skills in information security analysis by taking these top online courses
Here is a list of some of the best choices from Skill Success that can help you get started on working your way as an information security analyst:









